Product Introduction
PRODUCTS
The Challenge: Ever-Evolving Threats and Increasing Complexity
With constant changes in work environments and the growing sophistication and diversity of attack methods, cybersecurity has become a never-ending game of cat and mouse against new malware and unknown threats.
Common Challenges Facing Organizations Today
- Unknown malware that traditional antivirus software cannot detect
- EDR solutions that demand high operational effort and costly budgets
- Inconsistent security levels across departments and locations
- Human error that exposes risk despite multiple countermeasures
- Difficulty protecting legacy systems and unsupported operating systems
- Inability to apply patches immediately to UTM, VPN, and other network devices
- Delays in patching OSs and critical software vulnerabilities
As a result, security operations are becoming increasingly complex, and the conventional “detect and respond” approach has reached its limits.
Now more than ever, organizations need a completely new way of thinking about protection.
The Solution: From Detection to "Hardening"
We no longer call cybersecurity a battle.
The era of detecting and responding after threats infiltrate a system is already over.
What AppGuard delivers is "Hardening".
It creates a state in which the system simply does not accept any form of unauthorized interference—from malware-driven destruction to remote manipulation and unauthorized access by attackers.
In other words, instead of detecting attacks and chasing them down, AppGuard imposes operational rules that make attacks impossible to begin with. This is the answer AppGuard provides.
“Hardening” — Defense Without a Battle.
Hardening is a defensive concept that does not engage in battle with threats after they infiltrate, but instead creates an environment where threats cannot operate in the first place.
If traditional detection-based security is like installing a “security system” onto a building—monitoring for intrusions or suspicious behavior and sounding an alarm—then Hardening is a philosophy that reconstructs the building itself so that security is embedded into its very structure.
Inside this environment, only authorized users can take approved actions within permitted areas.
Any behavior that violates these rules is physically impossible, preventing attackers from achieving their objectives. Without identifying a threat or analyzing its behavior, the system simply maintains its normal, intended state at all times.
This is the fundamental advantage that Hardening provides.

Comparison Between Fortification and Traditional Approaches
| Category | Conventional Detection-Based Security | AppGuard’s “Hardening” |
|---|---|---|
| Security Philosophy | Focuses on how quickly the “intruder” can be detected after it breaks in. | Focuses on preventing any “malicious activity” from occurring within the system. |
| Handling Unknown Threats | Requires learning and defining new threats, often falling behind emerging attacks. | No threat definition required — even unknown attacks are rendered inactive. |
| Exploitation of Legitimate Tools | Aims to detect attacks and limit damage; however, vulnerabilities remain exploitable. | Neutralizes the specific commands needed to exploit vulnerabilities, preventing attacks from succeeding. |
| Role of Security Personnel | Primarily focused on alert analysis and incident response, requiring rapid reaction. | Prevents incidents before they occur, allowing teams to focus on proactive improvements. |
The Three Layers of Control Implemented in AppGuard
AppGuard verifies every command executed on a system in real time to determine whether it is legitimate and safe. Through this approach, it achieves the following three layers of control:
-
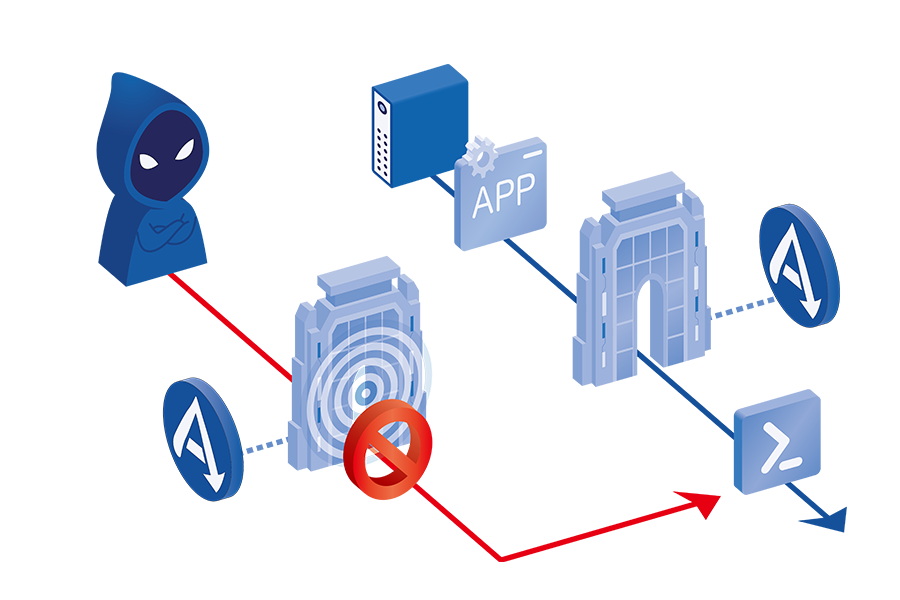
1. Launch Control
Prevents direct execution of legitimate tools—such as PowerShell—that could be exploited by attackers.
Even when such tools are required for legitimate business operations, they can only be launched via approved applications, effectively blocking the attacker’s “first move.” -
2. Behavior Control
Restricts applications that are frequently exploited in attacks, such as web browsers and Microsoft Office products.
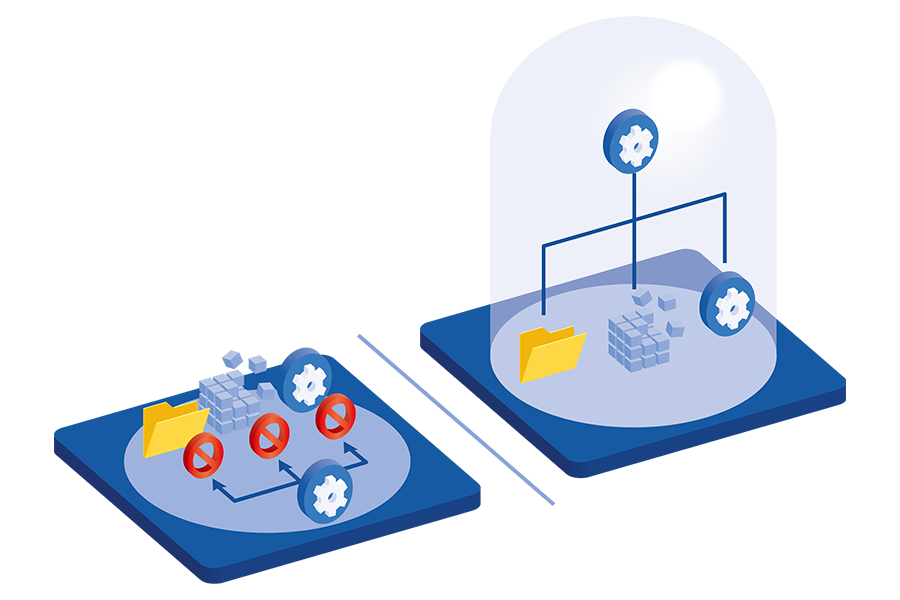
Even if compromised, these applications are prevented from performing critical actions such as writing to system folders or the registry, or manipulating the memory of other applications. Additionally, high-risk applications are executed within an isolated “secure space,” where accessible processes and resources are strictly controlled. -
3. Space Control
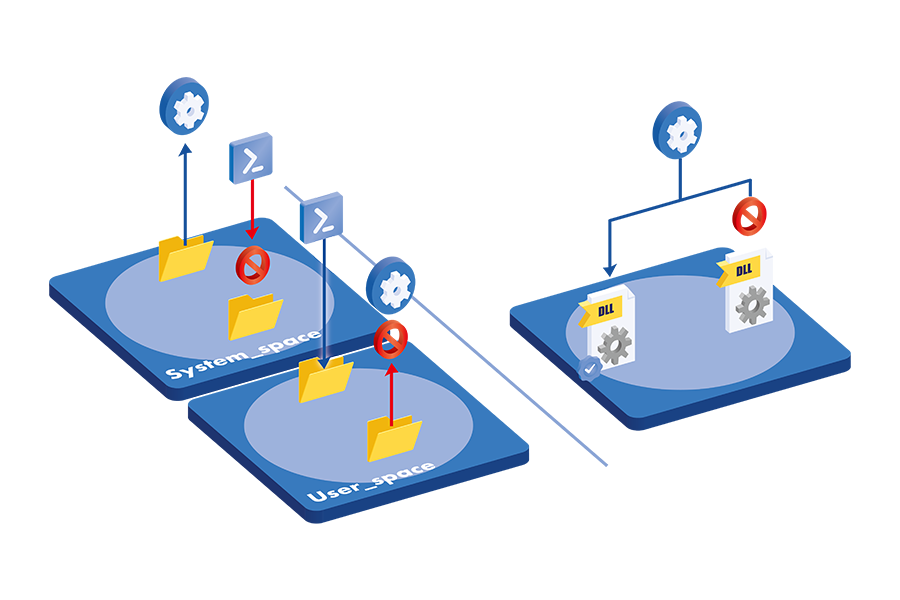
By default, execution of programs from untrusted locations—other than verified system folders—is prohibited.
Even if a malicious file is placed in a user directory, it cannot run without a valid digital signature or explicit full-path authorization.
This also prevents DLL side-loading attacks, in which unauthorized components are covertly loaded into legitimate applications.
Key Features of AppGuard
-
Execution-Prevention Architecture That Stands Firm Against Unknown Threats
AppGuard continuously validates program launches and behaviors in real time, instantly blocking any unauthorized actions.
Its three integrated mechanisms — Launch Control, Behavior Control, and Space Control — work interlocking to prevent attacks such as zero-day exploits and ransomware before they can even begin.
This represents an execution-prevention architecture that stops threats from ever materializing. -
Universal Defense Unaffected by Vulnerabilities or System Environment
AppGuard establishes protection by controlling the very commands essential for an attack to succeed.
As a result, it not only defends against attacks that exploit legitimate tools, but also enables mission-critical systems to operate securely even when immediate patching is not possible. -
A Scan-Free Security Platform That Keeps Systems Running Smoothly
Unlike traditional detection-based solutions, AppGuard requires no periodic scans or signature updates, eliminating unnecessary load on PCs and servers.
Security processes never interrupt business operations — ensuring a stable, seamless, and efficient system environment — because safety verification occurs instantly at runtime.
CasesCASE STUDY
- EBARA DENSAN CO.,LTD.
- Industry:Electrical and Mechanical Equipment Manufacturer
Product:AppGuard Enterprise
Water is essential to everyday life. EBARA DENSAN CO.,LTD., a company that has long supported Japan’s social infrastructure, developed "Rurion", a cloud service that optimizes the operation of water infrastructure in response to the growing challenge of a shrinking workforce.
- JTB Corp.
- Industry:Travel
Product:AppGuard Enterprise
Celebrating its 113th anniversary, JTB Corporation continues to take on the challenge of addressing social and regional issues through “Creating Opportunities for Exchange” on a global scale — delivering inspiration and empathy through travel experiences.
- JFE Steel Corporation
- Industry:Manufacturing
Product:AppGuard Enterprise
JFE Steel Corporation is driving digital transformation (DX) to strengthen its competitive edge. In parallel, the company is reinforcing security across its production sites—commonly referred to as OT environments—under the principle of “DX with Security,”
- Saitama Medical University Hospital
- Industry:Healthcare (Hospital)
Product:AppGuard Enterprise
In recent years, ransomware attacks have repeatedly struck medical institutions across Japan. In the worst cases, hospitals were forced to suspend regular medical services for extended periods of time. Witnessing these serious incidents firsthand, Saitama Medical University Hospital decided to move away from its reliance on the “closed network” myth and explore a more zero-trust-oriented approach.
Product LineupLINEUP
Frequently Asked QuestionsFAQ
- Q.
How should AppGuard be used in combination with antivirus or EDR solutions?
- A.
Antivirus and EDR solutions play an important role as detection and response layers in cybersecurity. AppGuard does not replace them — instead, it adds a new layer of “Hardening”, completing a truly multi-layered defense. To illustrate: if AV and EDR act as security guards who detect and respond to intruders, AppGuard serves as the architectural rule of the building itself, ensuring that even if an intruder gets inside, they cannot carry out any malicious actions. By combining AppGuard with detection-based solutions, you can build a last line of defense that addresses blind spots in conventional detection technologies and creates a far more resilient security posture.
- Q.
How long does it take to implement AppGuard?
- A.
For approximately 100 PCs, the implementation period is around one month.
For about 10 servers, it typically takes around three months.
However, the actual schedule may vary depending on several factors such as the number of PCs and servers, your network environment, and the number of installation sites.
We will propose a detailed implementation schedule after discussing your specific requirements.
- Q.
Can AppGuard be used together with other security products?
- A.
Yes, it can. AppGuard is designed to complement existing antivirus solutions as well as post-incident response products such as EDR and XDR, and can be used alongside them without conflict.
System RequirementsSISTEM REQUIREMENTS
| OS |
Please note that there are several restrictions regarding implementation in the editions listed below. For details, please contact support.
Implementation in the editions listed below requires verification by our company. For details, please contact support.
|
|---|---|
| Virtual environment | Please contact us individually regarding use in virtual environments. |
| CPU | A single-core processor with a clock speed of 1.80 GHz or higher, and an x86/x64 compatible architecture |
| Memory | 32bit OS 1GB以上 64bit OS 2GB以上 |
| ハード Disk |
100MB or more of free space |
| centralized management system |
included |
| Communications | This may vary depending on the usage environment and operational methods, so please contact us. |
(※1)
KB4474419 must be applied, or the KB number listed under “Package Details” on the following page must be applied.
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=38222b3b-2bd2-4269-880d-35feddf42984
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=3589375e-8147-4d21-b3ad-fc27bd126d6c
(※2)
KB914882 must be applied. Please contact us regarding obtaining the KB.
※It is assumed that multiple user accounts will not be logged on (signed in) to a single Windows terminal, nor will user switching operations be performed.
| OS |
Please note that there are several restrictions regarding implementation in the editions listed below. For details, please contact support.
Implementation in the editions listed below requires verification by our company. For details, please contact support.
|
|---|---|
| Virtual environment | Please contact us individually regarding use in virtual environments. |
| CPU | A single-core processor with a clock speed of 1.80 GHz or higher, and an x86/x64 compatible architecture |
| Memory | 32-bit OS: 1 GB or more 64-bit OS: 2 GB or more |
| Hard Disk |
100MB or more of free space |
| Centralized Management System | Included |
| Communications | Use either the HTTPS, FTP, or FTPS protocol for communication with the management server. |
(※1)
KB4474419 must be applied, or the KB number listed under “Package Details” on the following page must be applied.
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=38222b3b-2bd2-4269-880d-35feddf42984
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=3589375e-8147-4d21-b3ad-fc27bd126d6c
(※2)
KB914882 must be applied. Please contact us regarding obtaining the KB.
※It is assumed that multiple user accounts will not be logged on (signed in) to a single Windows terminal, nor will user switching operations be performed.
| 対応OS |
Installation on the following operating systems requires verification by our company. For details, please contact our support team.
Installation on the following operating systems requires a combination of AGMS v6.7.36 / v6.7.53 and v6.7.82 or later, along with Agent v6.7.149.1 or later.
|
|---|---|
| CPU | Single-core processor with 1.80 GHz or faster and x86/x64 compatible architecture |
| Memory | 32-bit OS: 1 GB or more 64-bit OS: 2 GB or more |
| Hard Disk |
100MB or more of free space |
| Centralized Management System | Yes |
| Communication | Use either HTTPS, FTP, or FTPS protocol for communication with the management server |
(※1)
KB4474419 must be applied, or the KB number listed under “Package Details” on the following page must be applied.
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=ac54099f-27ab-4e36-befd-a29c67ddeb6f#PackageDetails
※This installation must include the Desktop Experience.
※Use of SBC (Server Based Computing) is not covered by software support. Please contact us for individual support.
※When logging on to Windows Server with multiple accounts, there are prerequisites/limitations such as a maximum of two simultaneous sessions. For details, please contact support.
Embedded operating systems, including the Windows IoT Platform, require prior verification due to differences in libraries used by each company.
We provide verification tools. Please contact us individually with your OS information.
| OS |
|
|---|---|
| Virtual Environments | Please inquire individually regarding use in virtual environments. |
| CPU | Dual-core processor with 1.80 GHz or faster and x86/x64 compatible architecture |
| Memory | 32-bit OS: 1GB or more 64-bit OS: 2GB or more |
| Hard Disk |
100MB or more free space |
| Centralized Management System |
None |
| Communication | Internet connection required |
(※1)
KB4474419 must be applied, or the KB number listed under “Package Details” on the following page must be applied
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=38222b3b-2bd2-4269-880d-35feddf42984
https://www.catalog.update.microsoft.com/ScopedViewInline.aspx?updateid=3589375e-8147-4d21-b3ad-fc27bd126d6c